计算机病毒(中英对照)
COMPUTER VIRUS
It’s March 14,11:55 PM.A group of business partners are putting the finishing touches on an important report.After celebrating the completion of their efforts they identify a previously unnoticed typo.At 12:05 AM they turn the computer back on only to be greeted with a message saying“Beware the Ides of March.”[1] The hard drive spins furiously and the report is deleted by a computer virus.
Computer viruses are just one example of what is commonly referred to as malicious code or malicious programs.Malicious programs are created to perform a series of harmful actions on a computer system.Examples of some actions include file deletion,file corruption,data theft,and the less harmful but equally annoying practical joke.These programs often remain dormant and hidden until an activation event oclearcase/" target="_blank" >ccurs.Examples of activation events are program execution and specific access dates such as March 15,system reboot,and file access.When the predetermined activation event occurs,the malicious program begins its task.In the example above,this task was the deletion of all files in the computer system.
Theory behind Viruses
To better understand what a virus can do,it is helpful to understand how a virus performs its task.Fig. 18-4 contains a flow chart describing the basic actions of a virus.Each action identified in the figure is numerically labeled for explanatory purpose only.The order in which these actions are performed is indicated both pictorially,in Fig. 18-4 and in the discussion which follows.While the order of these actions may vary with each virus,the general process remains unchanged—perform an undesirable task and infect other programs and operating systems.
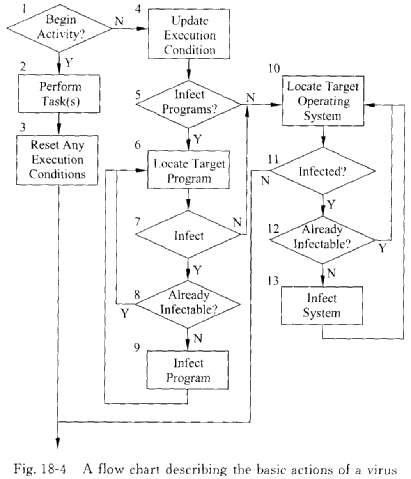
For this discussion two terms are defined:virus activation and virus execution.Virus activation will refer to the initiation of the virus.Virus execution,however,will refer to the initiation of the portion of the virus that performs the possibly harmful activity the code not directly concerned with infecting a system.[2] Thus,virus execution must be preceded by activation,but activation may not necessarily lead to execution.
Once an infected program is executed or an infected operating system performs a task,the virus is activated.The virus will first determine whether it should be executed.In the event that it should not be executed,it will attempt to locate and identify other susceptible programs,disks,or systems.Any such item will then be infected.After determining that all susceptible items carry a copy of the virus,the virus will stop and allow normal operations to proceed.If the virus meets all of its internal conditions to execute,it will do so.Upon completion of execution,the virus may either reset its conditions or remove itself.The virus will complete and allow normal computation to continue.While this process may seem time consuming and obvious to the user,it is not[3].Computers operate so quickly nowadays that this process may go easily unnoticed,and often does.
NOTES
[1]Ides of March指刺杀古罗马独裁者恺撒(Julius Caesar)的预示日(3月15日),即一个不吉利的日子。
[2]句中,由that引出的定语从句修饰它前面的portion;the code...是介词宾语to the initiation的补足语,中间被定语从句隔开。
[3]While引出的是让步状语从句。
KEYWORDS
typo 非正式的打印错
malicious code 恶意代码
malicious program 恶意程序
activation event 激活事件
system reboot 系统重新引导
EXERCISES
1.Multiple choices.
(1)Computer viruses are .
a.useful programs b.malicious code
c.malicious programs d.harmful programs
(2)Virus program consists of .
a.two parts b.three parts
c.four parts d.five parts
(3)The harmful actions performed by viruses include .
a.data theft b.practical joke
c.file corruption d.file deletion
(4)The virus execution is .
a.the virus activation
b.the code not directly concerned with infecting a system
c.the initiation of the portion of the virus
d.the code directly concerned with infecting a system
(5)The virus is activated when .
a.an infected program is executed
b.a computer is accessing a mailbox through the Internet
c.a computer is in shutdown status
d.an infected operating system performs a task
(6)Objects that are susceptible from the viruses are .
a.CPU b.disks
c.systems d.programs
(7)A virus program often remains .
a.dormant b.open
c.hidden d.awaked
(8)If a virus does not begin its activity,it .
a.stops its activity
b.performs its activity
c.updates its execution condition
d.finds the infect programs after updating its execution condition
2.True/False.
(1) Viruses can cause programs crashing or entire hard disk deleting.
(2) Some one died as the result of a computer virus.
(3) Before performing any actions you’d better treat all files and programs with virus check software.
(4) An infected computer may lose its data.
(5) In reality the viruses and their destructive capabilities have been grossly exaggerated by people.
答案:
1.
(1)b,c,d (2)a (3)a,b,c,d (4)b,c
(5)a,b,d (6)b,c,d (7)a,c (8)c,d
2.
(1)t (2)f (3)t
(4)t (5)t
翻译:
计算机病毒
3月14日晚11时55分,一群商业伙伴正在对一个重要报告进行最后的修饰,在庆祝他们完成使命之后,他们认出一个以前未注意到的打印错误。上午12时5分,他们再把计算机打开,不料面前呈现一条消息“当心不吉利的日子”,硬盘飞快地转动,随即该报告被计算机病毒删除了。
计算机病毒正是通常所说的恶意代码或恶意程序的一个例子。恶意程序的编写是对计算机系统实施一系列伤害动作的。例如文件的删除,文件的毁坏,数据的窃取以及伤害不大但完全令人讨厌的玩笑。这些程序往往处于休眠和隐藏状态,直到一个激活事件产生。激活事件的例子是程序的执行和专门发作日期,如3月15日,系统自举和文件读写。当预先确定的激活事件发生时,恶意程序便开始工作。在上面例子中,这一工作就是删除计算机系统中的所有文件。
病毒背后的理论
为了更好地知道病毒能做什么,了解病毒如何完成它的任务是有帮助的。图18-4所示是描述病毒基本动作的流程图。为了说明图中每个动作,都用数字标出。这些动作完成的顺序可用图18-4所示的图示方式指明,也可在下面讨论。虽然这些动作的顺序可能对每种病毒都不同,但一般过程保持不变一一完成一个不希望的任务并且传染给其他程序和操作系统。
根据这种讨论定义了两个术语:病毒激活和病毒发作。病毒激活是指病毒启动,而病毒发作是指可能造成危害动作的病毒部分的启动,该代码不直接去感染一个系统。因此,病毒发作之前必须激活,但激活不一定导致发作。
一旦受感染的程序被执行或者受感染的操作系统完成一项任务,病毒就会被激活。该病毒首先确定它应该在什么地方被执行,万一它不被执行,它将力图寻找并确认其他易受感染的程序、磁盘或系统。任何类似的对象将被感染。在确定易受感染的对象得到一份病毒的复制品之后,该病毒将停止并且让正常操作继续进行。如果满足了所有的内部执行条件,病毒就发作。发作完成以后,该病毒要么恢复其状态,要么自行删除。该病毒将结束并允许继续正常运算。这一过程可能看起来是费时的并且对用户来说是很明显的,其实不然。当今计算机的运算如此之快,以至这一过程很容易不被注意并经常如此。